SOCRadar is your early warning system
against external cyber threats
Free SOCRadar Tools
SOCRadar LABS is a new and developing platform which informs users about existing and possible cyber threats with the help of several cyber threat intelligence services.
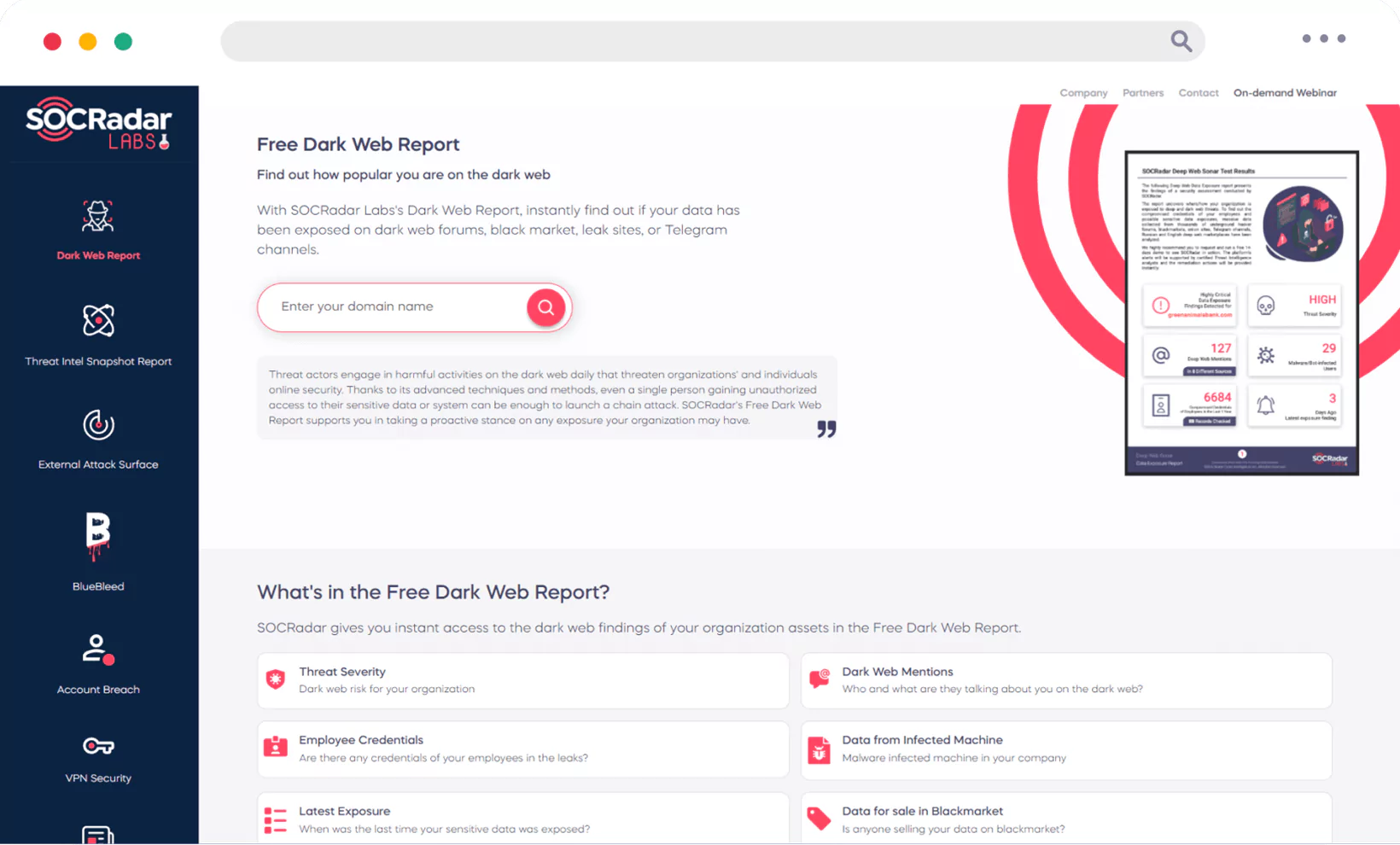
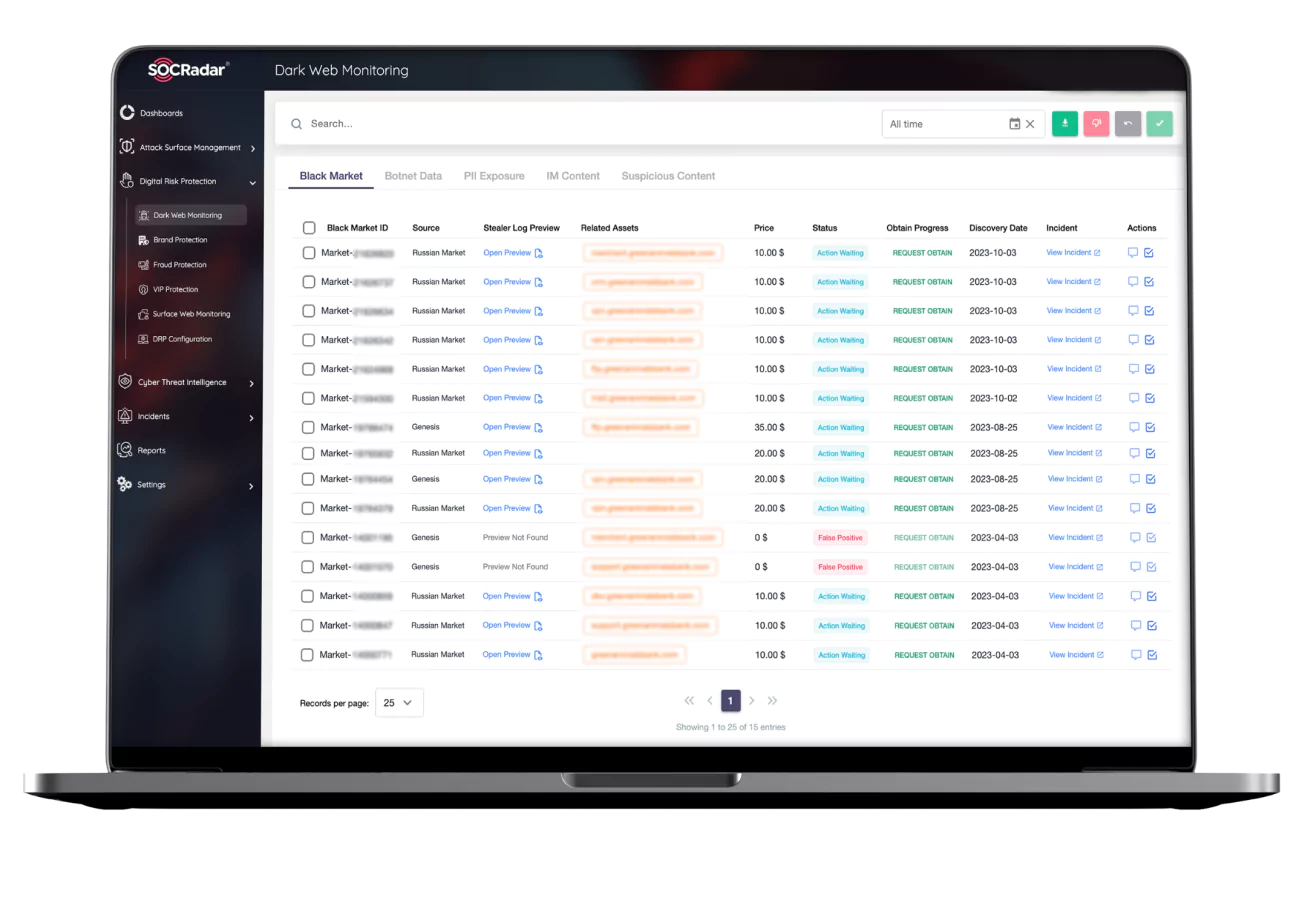
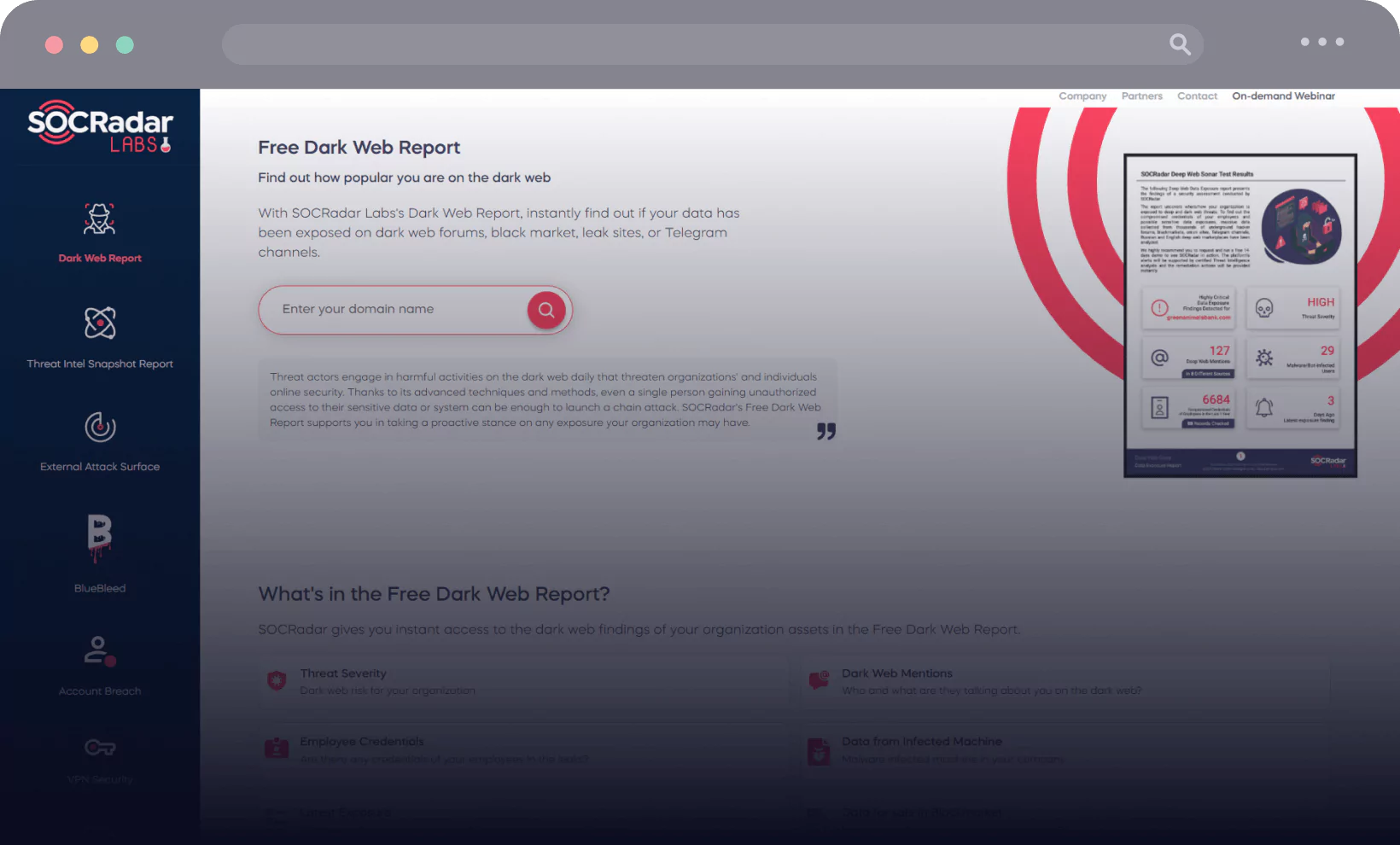
Dark Web Report
Dark Web Report
Discover the hidden threats with SOCRadar Labs’ Dark Web Report. In a flash, unveil if your data’s made an appearance in the shadowy corners of dark web forums, black markets, leak sites, or Telegram channels.
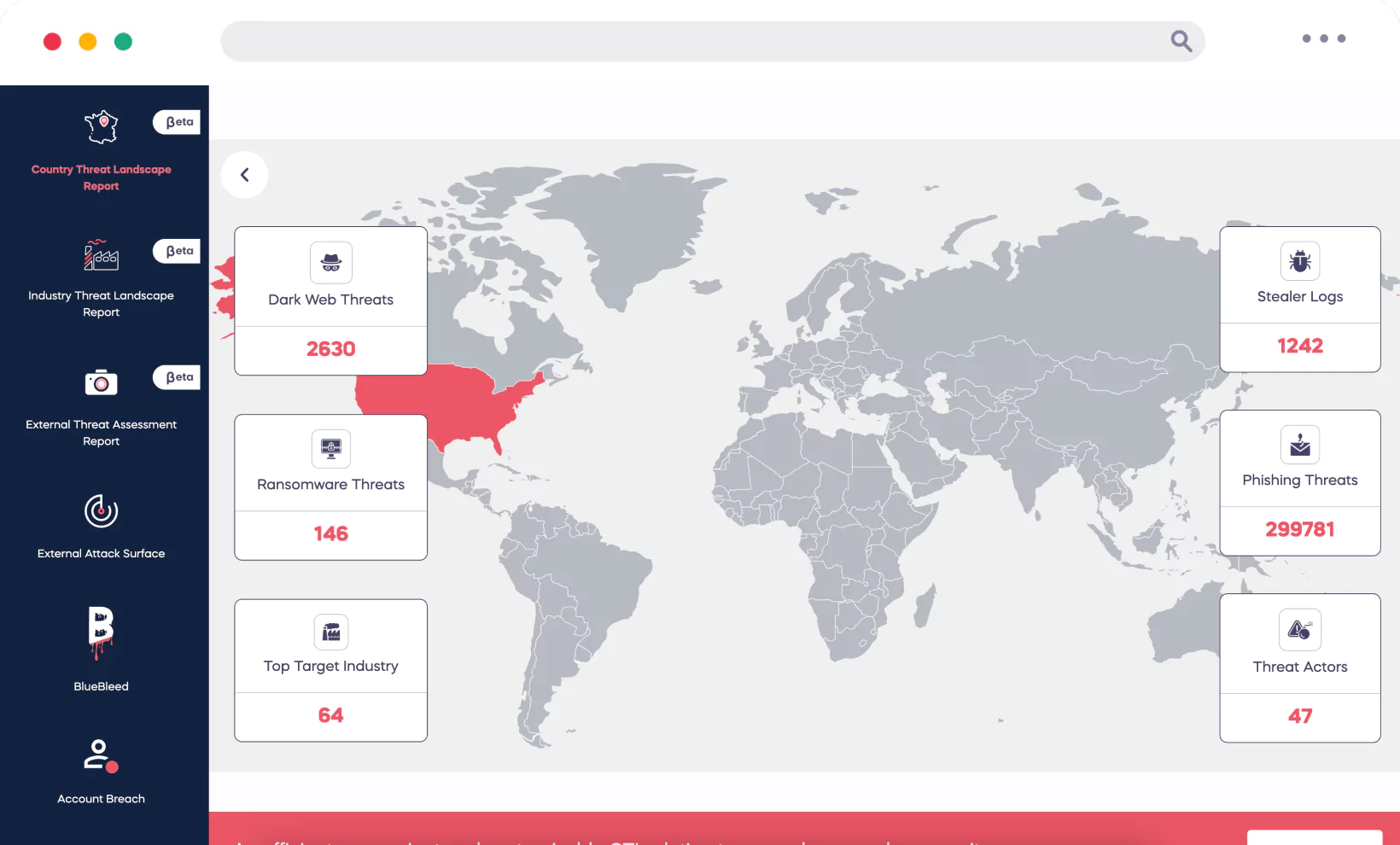
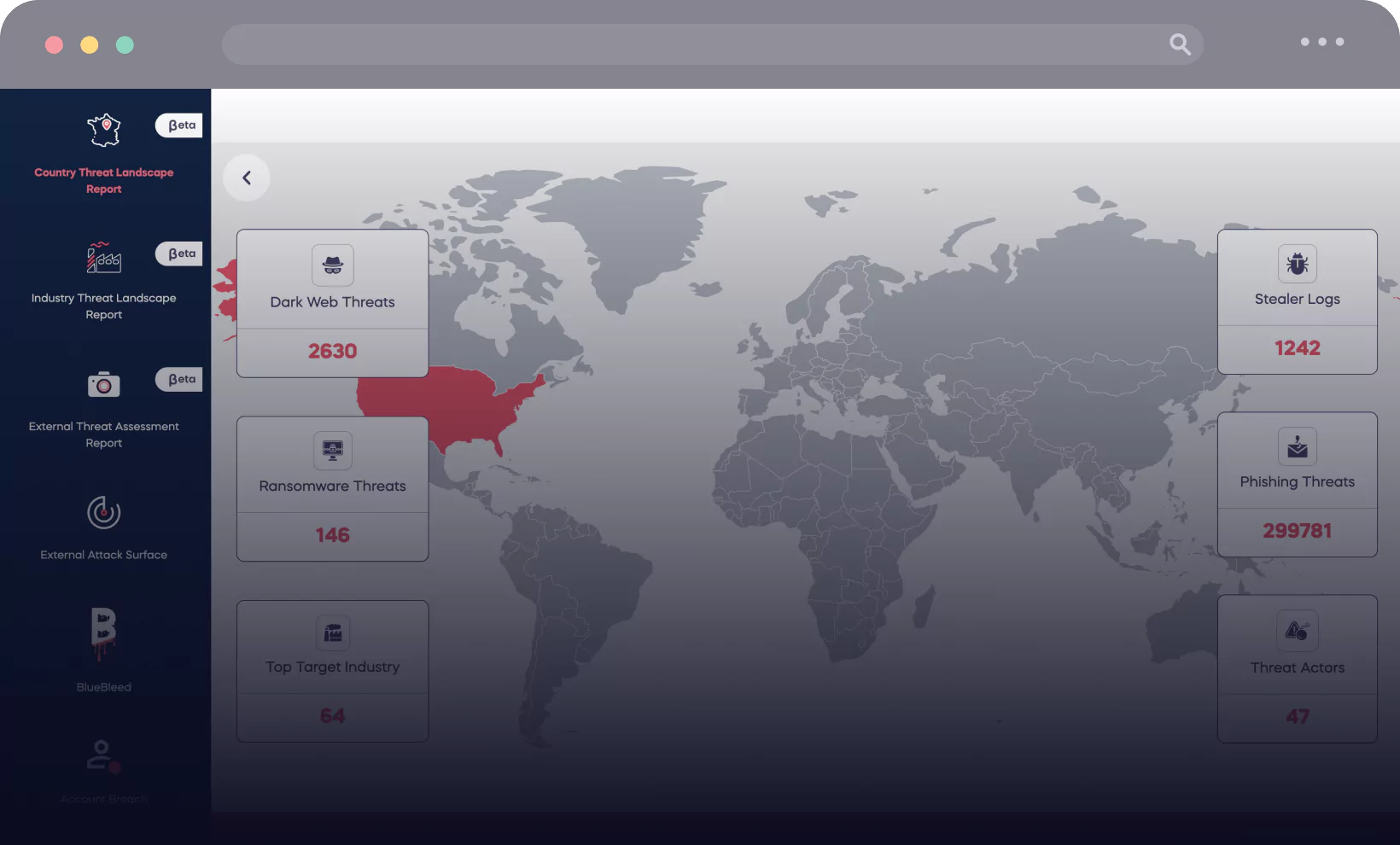
Country Threat Landscape Report
Country Threat Landscape Report
Illuminate your operational landscape with SOCRadar’s AI-powered Country Threat Report. In just a few seconds, unlock key insights into the digital dangers lurking in your company’s regions, from dark web threats to ransomware, phishing, rogue actors, stealer logs, and DDoS attacks.


Power up, protect, and future-proof your
organization with SOCRadar



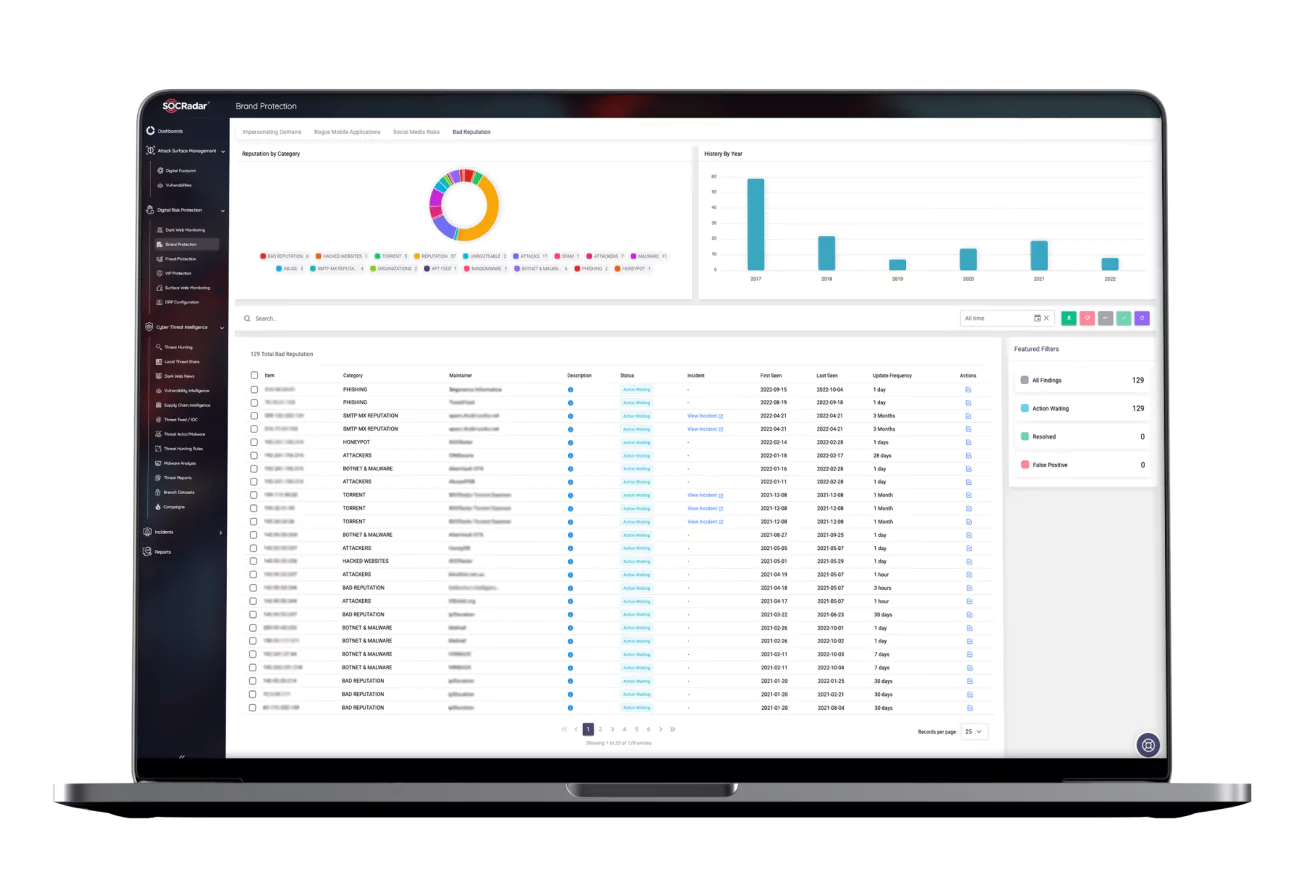
SOCRadar Advantages

306
Partners
150+
Countries
250M+
IP Search
1.6M+
Alarms


















































































It contributes significant benefits to our security posture. We are confident with actionable intelligence at fingertips. The monthly newsletters are useful and stable so far