
Tools and Features That Can Be Used To Detect Sensitive Data Leaks From Github – Part 2
In part 1 of this blog series, we discussed a few popular osint tools that help developer’s find leaked information from their GitHub projects: GitGrabber, GitLeaks, Gitminer, Gitrob. In this part, we will continue with another few tools and some examples for each.
TruffleeHug
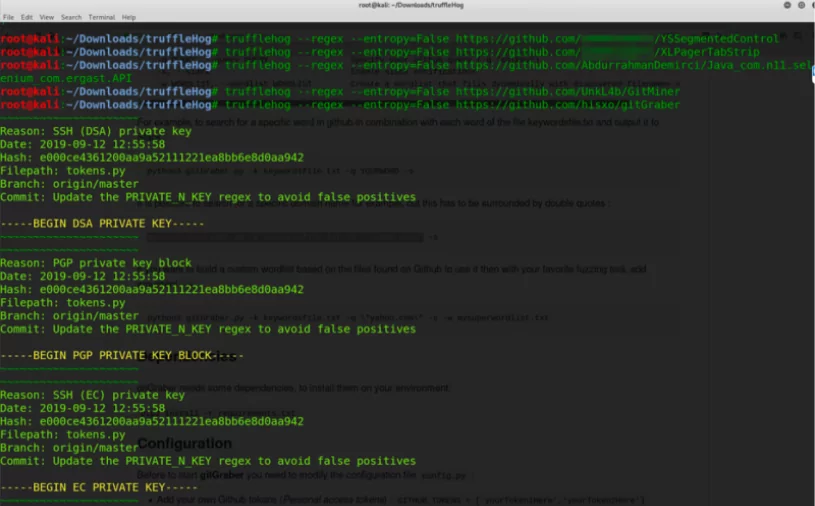
TruffleeHug is a tool used to find sensitive information that is accidentally committed or stuck on intermediate commits by digging into commit history and branches. Each branch’s commit history is checked. We can increase the commit depth using parameters. Since it works on a URL basis, it is among the target-specific tools.
In the example below, some repo that belongs to x-company have been dug but no leakage has been detected. For instance, when the repository of GitGraber is given, we can see that files like token.py that contain keyword list are detected.
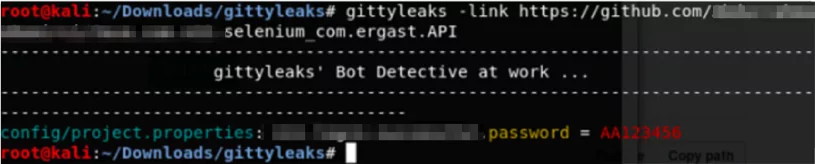
Gittyleaks
Username, password, and email that are in the repo can be detected by giving a clonable link/user repo link. There is password detection with a good success rate which hasn’t come as alerts at SOCRadar. If we want to use it effectively, we need to identify the repo of the company employees.
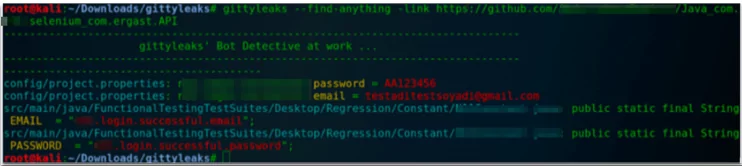
If it is needed, we can ask to dig anything that you find suspicious.
Github Dorks
This is a collection of dorks to search for sensitive data on GitHub repos. Scanning can be done by giving a user repo, company name, or direct link. In the dorks’ list, there are file name examples and Google Dorks searches through that list. Scanning doesn’t last for too long. For example, for a small company, scanning may last for about 2 minutes. It doesn’t seem to be very successful, and compared to GittyLeaks it actually is unsuccessful. But it’s still worth trying.
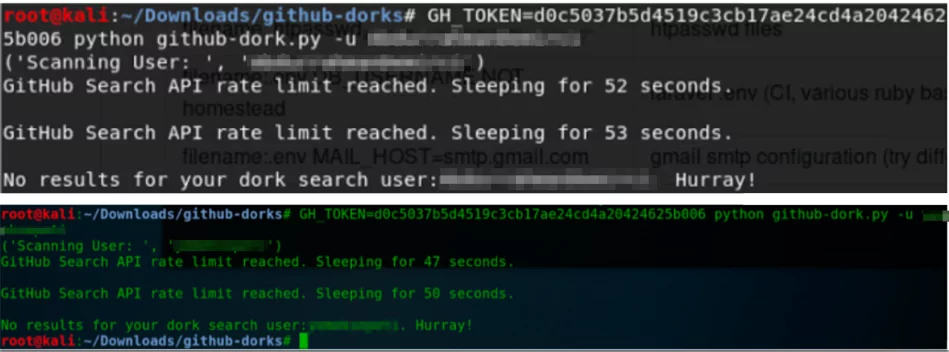
python github-dork.py -u → All repos belonging to the company/an employee can be defined with the name of the repo where the company takes place.
Repo Scanner
Reposcanner is a python script to search through the commit history of Git repositories looking for interesting strings such as API keys, inspired by truffleHog.
Repo Scanner is a tool to dig passwords, private keys, and similar sensitive information in Github. The process flows as follows: the wanted repo is firstly downloaded to local, then the commands are executed by going into the downloaded folder. An example done for n11 is given in the picture.
Digging process can be done for all files in a folder.



































