Types of Threat Intelligence Gathering
For better security functioning, all organizations need reliable but also real-time cyber threat intelligence. Producing threat intelligence is a complex process and goes through a 5-staged cycle. We have previously written a blog explaining each stage’s importance and given further detail – you can find it here. All stages contain almost equal importance about the well-functioning of this cycle, but some of them are a bit more difficult to process.
In this blog, we will discuss one challenging stage, and that is information gathering, or also known as the collection stage.
Gathering the right information to produce intelligence, is the key to better decision-making for every company, in every industry – no exceptions.
In the information-gathering step, there are a few disciplines used for collecting intelligence – the INTs. We gather information using various techniques and tools. These disciplines are pretty distinct. There is information gathered from people, from intercepted signals, open sources, and other sources as well.
From HUMINT to SIGINT, OSINT, or GEOINT we will discuss all of them in short points and explain to you what they are, their importance, and what are some possible sources.
HUMINT

Human Intelligence (HUMINT) is one of the many disciplines of information-gathering, one of the oldest ones. It relies on people, so it requires almost no technological product. The collection of information can be in the form of questioning people, but also in the form of espionage.
Companies usually use it to get information from people they suspect know additional sensitive information crucial for answering organizational questions.
If you want to understand the importance of HUMINT better, here is a use case for you – a threat actor asks for a ransom and threatens you with a data breach. Wouldn’t it help, first, to check if that demand for ransom is legitimate or not, and check if that breach is possible or just a decoy? There are many ways to find that out, and one of them is by interacting with the threat actor – so finding information through HUMINT.
GEOINT / IMINT
Geospatial Intelligence (GEOINT) and Imagery Intelligence (IMINT), help you keep track of any satellite system’s activity, and check for vulnerabilities as well.
GEOINT is the type of information-gathering discipline that evaluates geospatial information related to activities happening on the earth. Sources like satellites, maps, signals, and even IMINT sources help you get GEOINT information.
Out of many sources, the first one that should come to your mind is Google Maps. This tool is one of the free geospatial services you can use in your investigations.
On the other hand, IMINT, or lesser-known as Photo Intelligence (PHOTINT), includes collecting electro-optical, radar, or infrared images and analyzing those graphical data. Organizations usually use it to provide information about the location where a threat occurs.
MASINT
Measurement and Signature Intelligence (MASINT) is a discipline more focused on industrial activities. It is information gathered from sensors that record signatures of set targets.
Different electro-optical sources, radars, acoustic sensors, and similar, are examples of how MASINT can be collected. MASINT also leverages data used from IMINT and SIGINT as well.
The collected information using MASINT describes characteristics of events like nuclear explosions. It also finds obscure features of weapon systems. As you can understand, military services are the ones that leverage this type of information-gathering discipline more than other services.
OSINT
Any information gathered from publicly available sources falls into Open-source Intelligence (OSINT). OSINT is a provider of valuable organizational information regarding its activities, capabilities, and technical processes.
The information gathered through this discipline is very helpful for strategic decision-making.
An OSINT source is everything that is public to everyone that includes information obtained from the media, free stuff on the internet, government reports, official declarations, research papers, newsletters. And the list goes on and on…
An obvious problem here is the breadth of information. There are zillions of tools, and sources you can get information from, therefore it is sometimes difficult to find reliable sources. This is why you need to keep in mind that you need to review the data a little bit more carefully.
SOCMINT
Social Media Intelligence (SOCMINT) is information gathered from different social networking sites. This discipline falls under OSINT because it is mainly open-source information.
SOCMINT is very helpful for getting information about a company, its employees, potential partners, and being on track with their activities. Not just that, organizations can also track discussions that threat actors do about them, and be aware in case any of these discussions intends reputational damage.
Possible sources where you can gather SOCMINT information are all social networking sites that most of us use every day.
SIGINT
Collected by intercepting the signals, Signal Intelligence (SIGINT), collects either direct communication between two people, or electronically transmitted communication. This discipline includes COMINT, ELINT, and FISINT as well.
Communication Intelligence (COMINT), is used to obtain information regarding the sender, receiver, location, time, duration, and similar other data from an interception of foreign communication. Airwaves, cable, fiber optics, and other mediums are examples of COMINT sources.
Electronic Intelligence (ELINT) is used to get information using electronic sensors and is usually used to find the location and characteristics of a target.
Foreign Instrumentation Signals Intelligence (FISINT) is used to gather signals that may contain telemetry data of weapons or other remotely controlled devices.
TECHINT
Technical Intelligence (TECHINT), helps you to obtain better knowledge regarding adversary technical capabilities. It gives you the option to develop technological advantage and effective countermeasures.
Adversary equipment is the main source for gathering TECHINT. And this is why this discipline is highly effective.
Other sources can be satellites, technical research papers, and even human contact.
Since the information comes directly from the adversary, it is extremely useful to neutralize the adversary’s technological advantages.
FININT
Financial Intelligence (FININT) helps organizations obtain information about the adversary’s monetary transactions.
Possible sources for gathering this kind of information are, of course, banks, SWIFT, and usually the Financial Intelligence Unit (FIU).
Information gathered from FININT helps your company predict the adversary’s intentions and know its financial sources.
We are living in a time when technology is continually developing, so information gathering tools improve day by day. However, the nature of these disciplines has been this way for years, and they carry great importance for every analyst.
Every company needs to understand what kind of information they need to collect, then select the right tools and discipline, and start to work on intelligence.
After information-gathering, it is extremely important to do the required analysis and transform the raw data or information into actionable intelligence. If you still think that information is enough for decision-making, and still use the terms information and intelligence interchangeably, you can read our blog about the difference between them.
Learn more about SOCRadar’s intelligence gathering capabilities
SOCRadar’s Threat Intelligence module provides a rich context added on top of automation-powered information gathering. We use different OSINT tools to generate threat intelligence feeds such as phishing domains, malicious IPs, hacked websites, hashes, and DDoS attackers.
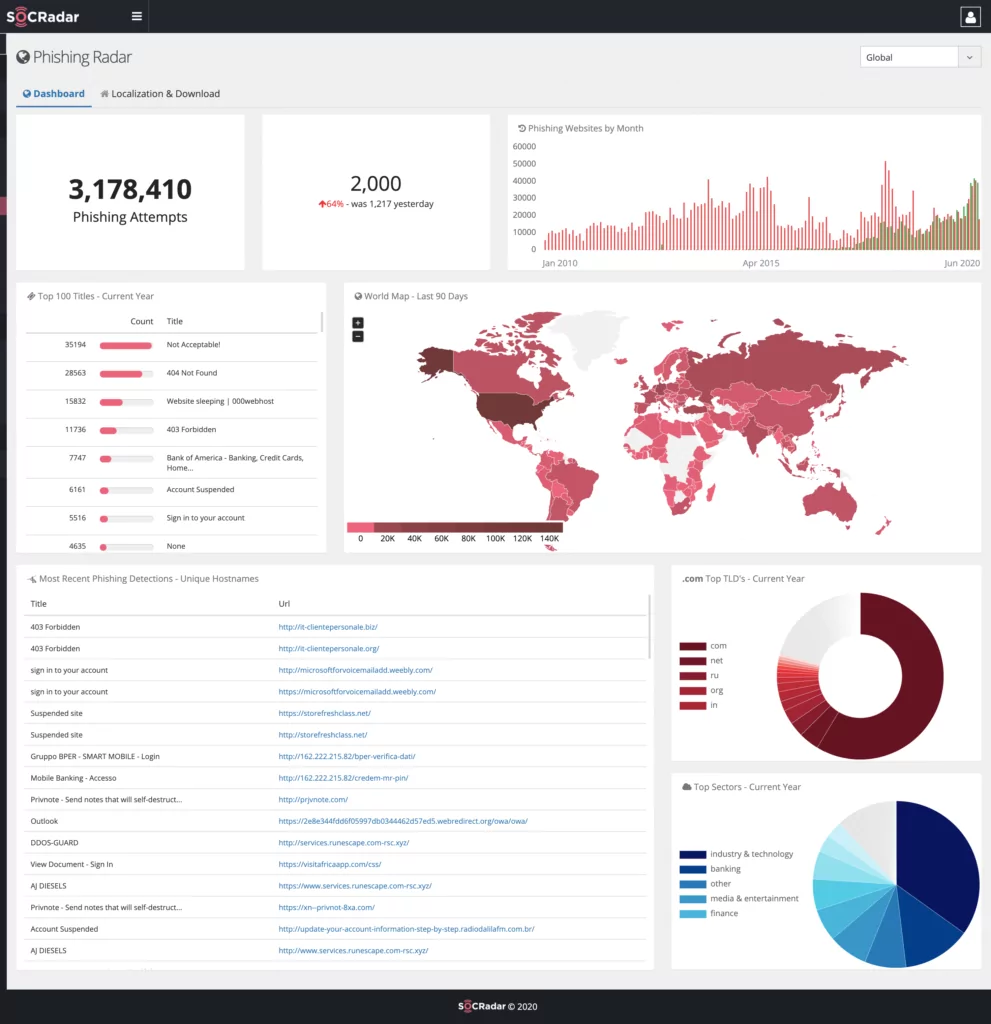
You can leverage this module to know more about what’s going on around the cyber world. SOCRadar uses SOCMINT to gather the latest and popular security-related posts to then inform companies about them. In the Threat Intelligence module, a robust dashboard with information about popular threat actors keeps TI teams up to date on the latest threat actor activities.
Get an insight into threat actors’ goals by leveraging our comprehensive range of threat intelligence.
Be aware of what’s going on around the cyber world. Get Started